

Packet Analysis
Analyzes a network packet and examines its content to detect the presence of malicious data. If a threat is detected, it triggers an appropriate response.
Packet Analysis Advantage :
1. Attack detection:
It is used to analyze network packets
and check for suspicious or potentially suspicious
payloads. This is done by examining the packet. If a
suspicious payload is detected, an alert is generated
indicating the discovery of malicious data in the network
packet and an appropriate response is given.
2. Execution of preventive measures:
When malicious data
is detected, preventive measures are taken to deal with the
potential attack.
3. Event analysis and logging:
In addition to immediate
preventive actions, events are also logged and displayed on
the user interface.
Overall, this program helps improve network security and protect it from attacks and malicious software. It also provides valuable information for understanding attack patterns and analyzing them to take future preventive measures..
Attack Detection
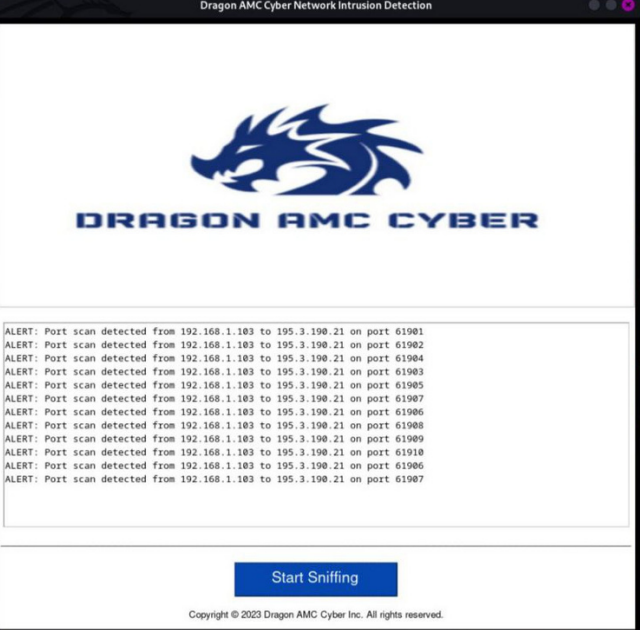
It analyzes network packets to detect different types of network attacks and give an automatic response
Attack detection Advantage
This program is of great importance in the field of network security. It analyzes network packets and detects potential attacks. With this program, it is possible to detect and identify common attacks and take appropriate actions to deal with them. Here are some examples of its importance:
1. Detection of Port Scanning Attacks:
The program can monitor
unauthorized attempts to scan ports on network devices. This allows
the administrator or user to be alerted to the presence of an attacker
trying to exploit system security weaknesses.
2. Detection of Distributed Denial of Service (DDoS) Attacks:
The program can monitor abnormal traffic and detect DDoS attacks
targeting network devices or servers. This allows measures to be taken
to mitigate the impact of these attacks and protect the stability of services.
3. Detection of Internet Control Message Protocol (ICMP) Flood
Attacks:
The program can monitor abnormal traffic associated with
flood attacks on the Internet. This allows the user or administrator to
be alerted to the presence of attacks aimed at disrupting the network or services.
4. Detection of Address Resolution Protocol (ARP) Spoofing Attacks:
The program can monitor attempts to spoof the ARP protocol, which aim to
steal MAC addresses or illegitimately redirect traffic. This allows for the
detection of phishing attacks and the protection of the network from intrusions.
Port Scanning
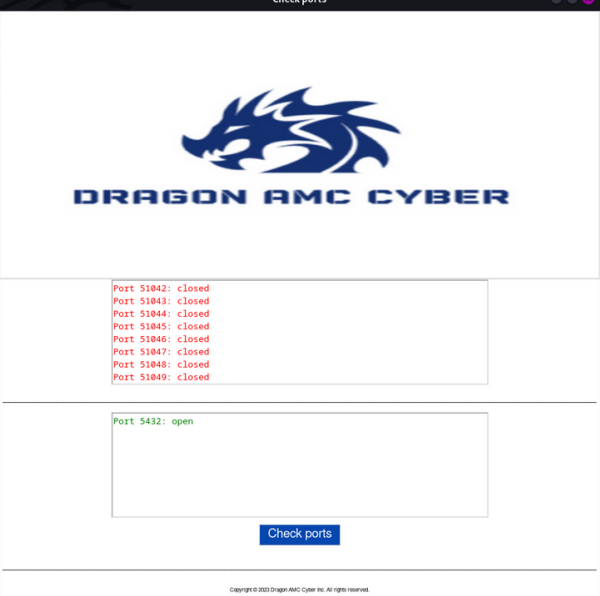
It checks the status of network ports on the local computer. This helps identify any open and closed ports, and is useful for testing, verifying network security, and identifying potential vulnerabilities. It can also be used to verify that services are running on the required ports